WordPress is the most popular content management system on the web. It powers over 60% of all sites using a CMS, which means roughly 43% of all websites run on this platform.
Since WordPress holds such a large market share, it naturally increases the likelihood of hacking attempts. Security is not something to take lightly, and trust me, you don’t want to experience your website being hacked.
Securing your site involves a series of steps. But before we dive into those actions, the question arises: is WordPress secure out of the box?
Is WordPress Secure?
Due to the frequent attacks on WordPress sites, many wonder if it is secure enough. To put it simply, WordPress itself – especially its core files – is well-built to make it difficult for hackers to exploit.
Most successful hacks on WordPress sites result from human errors, incorrect configuration, or improper maintenance. The main reasons sites become vulnerable include outdated WordPress versions, outdated plugins, and the use of plugins or themes from inexperienced developers.
So where is WordPress most vulnerable? According to Patchstack’s 2025 report, 89% of all WordPress vulnerabilities originate from plugins, 11% from themes, and less than 1% from WordPress core. Over 57% of these vulnerabilities require no authentication to exploit.
In this guide, I will share several steps to strengthen your website’s security and make it harder for hackers to succeed.
17 Actions to Strengthen Security on WordPress Sites
While there is always a chance your site could be hacked, and you can never prevent it entirely, there are several best practices and actions you can take to make hacking attempts significantly more difficult.
1. Choose the Most Expensive Hosting You Can Afford
Even if you take all the security steps, if you don’t have reliable hosting, your efforts may not help much. A significant percentage of WordPress sites are compromised due to vulnerabilities in their hosting environment.
If you are on shared hosting, make sure your host offers account isolation. This prevents a compromised site on the server from affecting your WordPress site.
A better option is managed WordPress hosting, where there is a higher likelihood of having a firewall tailored for WordPress, up-to-date PHP versions, routine malware scans, a server optimized specifically for WordPress, and a support team that knows WordPress inside and out.
2. Use the Latest Version of PHP
PHP is the language WordPress is built on, so using a supported version on your server is crucial. Each major version of PHP is supported for about four years after its release (two years of active support plus two years of security-only support).
As of 2026, PHP 8.1 and older are end-of-life and no longer receive security patches. PHP 8.2 is in security-only support (until December 2026), while PHP 8.3 and 8.4 are the recommended versions.
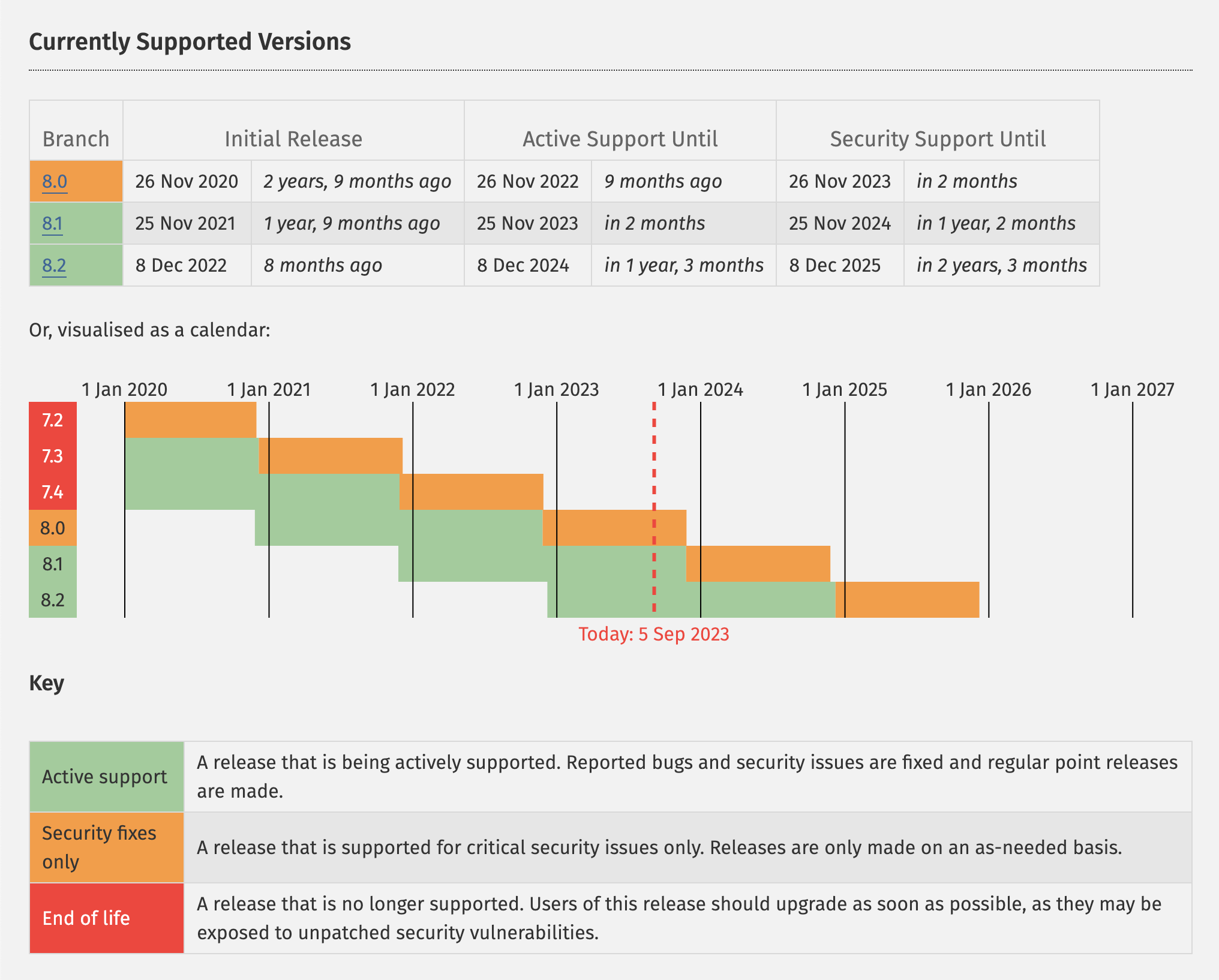
Make sure you are running at least PHP 8.2, and upgrade to 8.3 or 8.4 when your hosting provider supports it.
There is also a performance difference between PHP versions. Using a newer PHP version can boost your WordPress site’s speed and performance.
3. Ensure WordPress and Plugins Are Up-to-Date
It is crucial that your WordPress site runs the latest version of WordPress, as well as the latest versions of your plugins. Beyond that, only use plugins and themes from trusted sources. Install themes and plugins only from the WordPress repository, and choose those with many active installs and high ratings.
If your site is running outdated versions, you are more exposed to hacks because attackers tend to target older versions with known vulnerabilities.
Equally important – always back up your site! A backup allows you to quickly restore your site if it gets hacked.
4. Use Strong Passwords and a Password Manager
Be smart when choosing your admin username and password. Don’t use “admin” as the username, and choose a complex password. This is probably one of the most important actions to prevent hacks, and ironically, it is the simplest to implement.
Use a password manager like 1Password, Bitwarden, or LastPass to generate and store strong, unique passwords. Never reuse the same password across multiple sites.
5. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds a second layer of security beyond your password. Even if an attacker obtains your password, they cannot log in without the second factor.
The recommended approach is app-based authentication (TOTP) using apps like Google Authenticator, Authy, or Microsoft Authenticator. Avoid SMS-based 2FA when possible, as it is vulnerable to SIM-swapping attacks.
You can enable 2FA using plugins like WP 2FA, Two-Factor, or through security plugins like Wordfence and Solid Security that include 2FA as a built-in feature.
WordPress.org now requires two-factor authentication for all accounts with publishing capabilities. This reflects how critical 2FA has become for WordPress security. If you have not enabled 2FA on your site yet, do it now.
6. Change the WordPress Admin Login URL
To prevent brute force attacks, it is a good idea to change the login URL for your WordPress admin panel. Since the default login page is wp-admin, hackers try various combinations of usernames and passwords at this URL to attempt breaking into your site.
You can make it harder for them by changing the login URL. You can easily do this with a plugin like WPS Hide Login.
Check out my quick guide on how to change the WordPress admin login URL using WPS Hide Login.
7. Limit the Number of Login Attempts
By default, WordPress allows unlimited password attempts, which makes your site vulnerable to brute-force attacks.
You can easily implement a login attempt limiter using a dedicated plugin, such as Limit Login Attempts Reloaded.
8. Secure the wp-config.php File
The wp-config.php file contains all the information needed to access your site’s database. This is the most important file in your WordPress installation.
Secure the file by preventing direct access. Add the following to your .htaccess file:
<Files wp-config.php>
Require all denied
</Files>Editing the .htaccess file is recommended for advanced users only.
9. Disable XML-RPC
XML-RPC is a legacy protocol that allows remote access to your WordPress site. It has been entirely superseded by the REST API, which provides more secure, token-based authentication.
Hackers can exploit XML-RPC to perform brute-force attacks (using system.multicall to test hundreds of passwords in a single request) and DDoS attacks via pingbacks.
You can disable XML-RPC with a plugin like Disable XML-RPC-API or by adding the following to your .htaccess file:
<Files xmlrpc.php>
Require all denied
</Files>Unless you specifically use tools that require XML-RPC (like the WordPress mobile app or Jetpack), disable it.
10. Hide Your WordPress Version
WordPress updates usually contain security fixes. If you check your site’s source code, you will find that your WordPress version is visible in a meta tag.
This information is available to hackers, giving them insights if they are looking to target sites using older WordPress versions with known vulnerabilities.
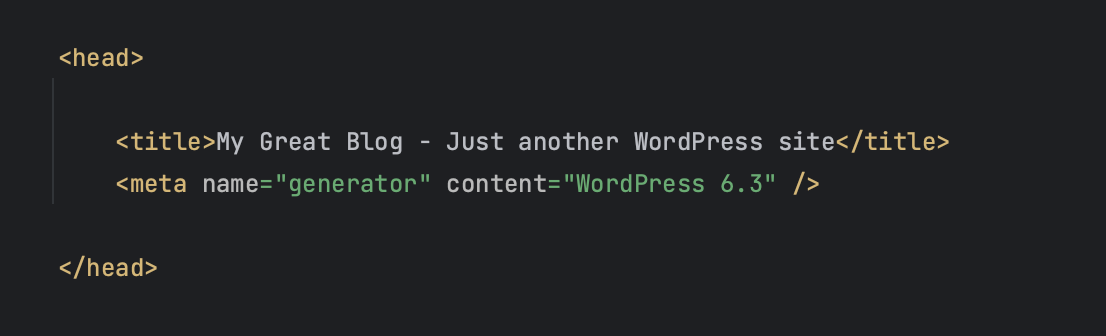
To hide the WordPress version, add the following code to your functions.php file:
function wpversion_remove_version() {
return '';
}
add_filter('the_generator', 'wpversion_remove_version');11. Use a Security Plugin
There are many WordPress security plugins available that handle several of the tasks mentioned in this guide and help prevent brute force attacks while strengthening your site’s security.
These plugins can block malicious networks, prevent security holes, enforce strong passwords, scan for changes in core WordPress files, set up a firewall, monitor DNS changes, and more.
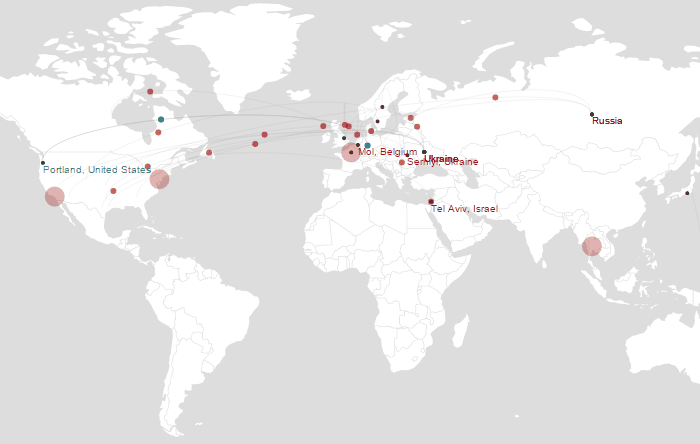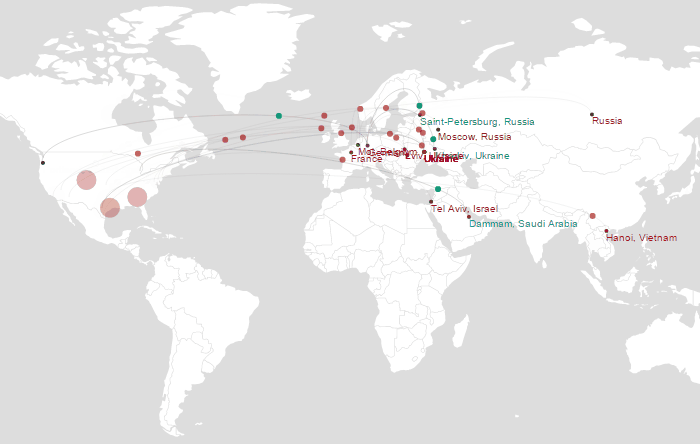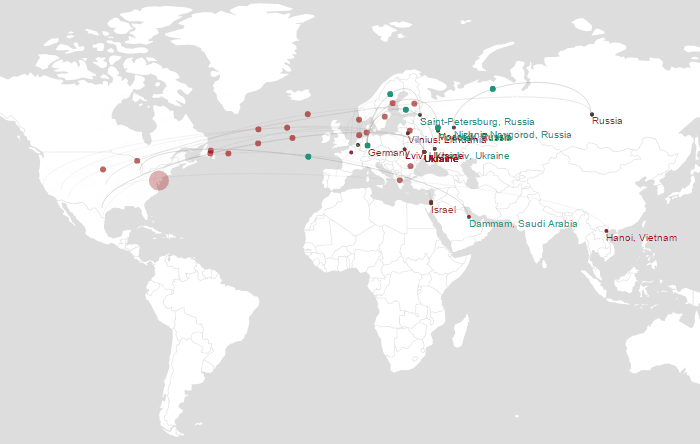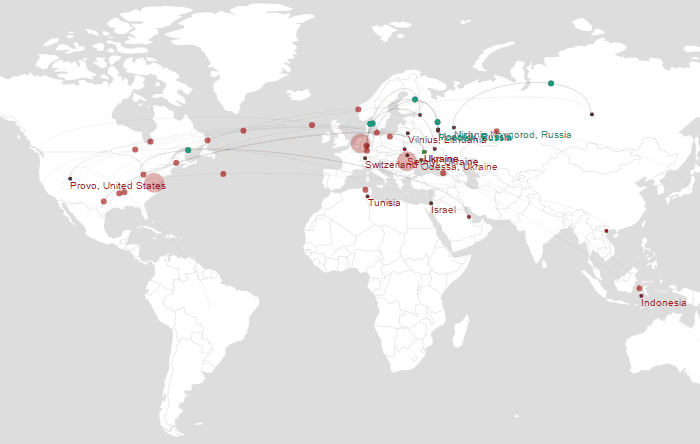
Source: Wordfence Real-Time Traffic
Here are some recommended security plugins:
- Wordfence Security
- Solid Security (formerly iThemes Security)
- Sucuri Security
- Shield Security
12. Always Use a Secure Connection
No matter where you are connecting from, always ensure that the connection to your server is secure. Use encrypted SFTP (or SSH) to access your site’s files. Your hosting provider should offer secure tools for server access.
When I say secure, I mean using supported and up-to-date versions of PHP and MySQL, isolating accounts, and using firewalls. Avoid cheap shared hosting, as it can result in issues like overloaded servers and shared IP addresses.
13. Disable File Editing from the WordPress Dashboard
Users with admin privileges can edit the PHP files of themes and plugins directly from the WordPress dashboard. It is recommended to disable this feature and only edit files via FTP.
To disable file editing, add the following line to your wp-config.php file:
define('DISALLOW_FILE_EDIT', true);14. Hide Login Error Hints
When trying to log into WordPress with an incorrect username or password, WordPress displays a message telling you which part is wrong.
This message gives hackers a clue as to which detail is incorrect. You can change these messages to a generic one by adding the following function to your functions.php file:
function no_wordpress_errors(){
return 'Wrong Details - Try Again';
}
add_filter( 'login_errors', 'no_wordpress_errors' );15. Use an SSL Certificate to Encrypt Data
Implementing an SSL certificate is crucial for securing your WordPress dashboard. SSL ensures encrypted and secure communication between the user, the browser, and the server, making it harder for hackers to intercept and steal information.
In many cases, an SSL certificate is available for free with your hosting package, usually through Let’s Encrypt.
SSL certificates also affect your WordPress site’s ranking in Google, giving a higher ranking to sites with an SSL certificate. Here is an article that explains SSL certificates and their importance for WordPress sites.
An SSL certificate is also part of the important transition to the HTTPS protocol, which has benefits beyond securing communication.
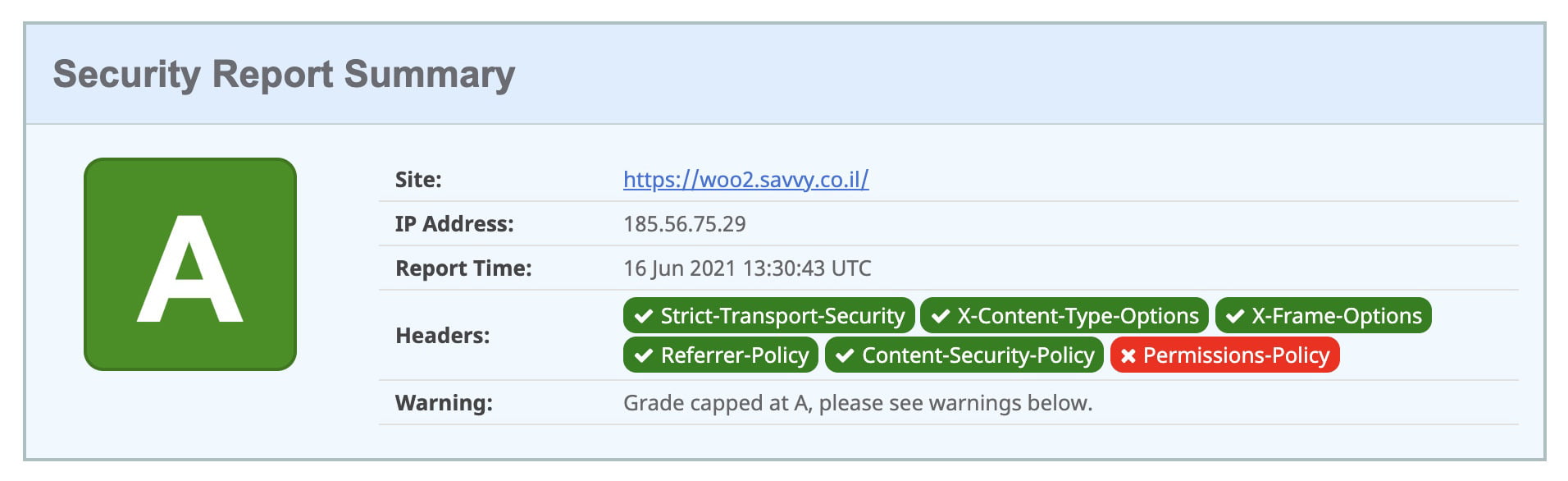
16. Add Security Headers
Security headers in WordPress are designed to protect applications from common attacks without requiring changes to your application’s code. Though it is the last action chronologically in this post, it is definitely one of the first and most important things to do.
Check out the post I wrote on adding security headers to WordPress sites.
17. Secure the WordPress REST API
The REST API allows developers to interact with your site’s data, which is great for headless setups, AJAX, and integrations. But if left unsecured, it can expose sensitive information such as usernames, unpublished posts, and more.
By default, unauthenticated users can access various REST API endpoints, which may lead to enumeration or data scraping attacks.
There are several ways to limit and secure REST API access, including:
- Allowing access to authenticated users only
- Blocking specific endpoints like
/wp-json/wp/v2/users - Hiding sensitive user data such as emails and display names
- Using security plugins to control REST access without writing code
To learn how to safely lock down the REST API without breaking theme or plugin functionality, check out our full guide on securing the WordPress REST API.
Do not disable the REST API entirely. WordPress core features like the block editor (Gutenberg), many plugins, and the WordPress admin itself depend on it. Instead, restrict access to specific endpoints or require authentication where needed.
FAQs
Common questions about WordPress security:
Summary
As you can see, there are many actions you can take to strengthen the security of your WordPress site. Many of the recommendations take only a few minutes to implement, so do them to ensure you have better peace of mind about your site’s security.
I hope you found this guide helpful. Feel free to comment and share, and I’d love to hear any additional tips you have so we can all learn together 🙂


